4.7. Configuring the RADIUS access to the LinOTP appliance#
A RADIUS client is a device that connects to the LinOTP server for authentication purposes using the RADIUS protocol. This protocol is (or can be) implemented in a wide range of login procedures e.g. SSL VPN, firewall or the LinOTP Authetication Provider for Windows (LAP).
The Appliance includes a preconfigured freeRADIUS server. For security reasons
no RADIUS client is accepted by default. So you need to configure who is
allowed to contact the LinOTP Server via the RADIUS and which secret
should be used to secure the RADIUS client-server connection. This can be done
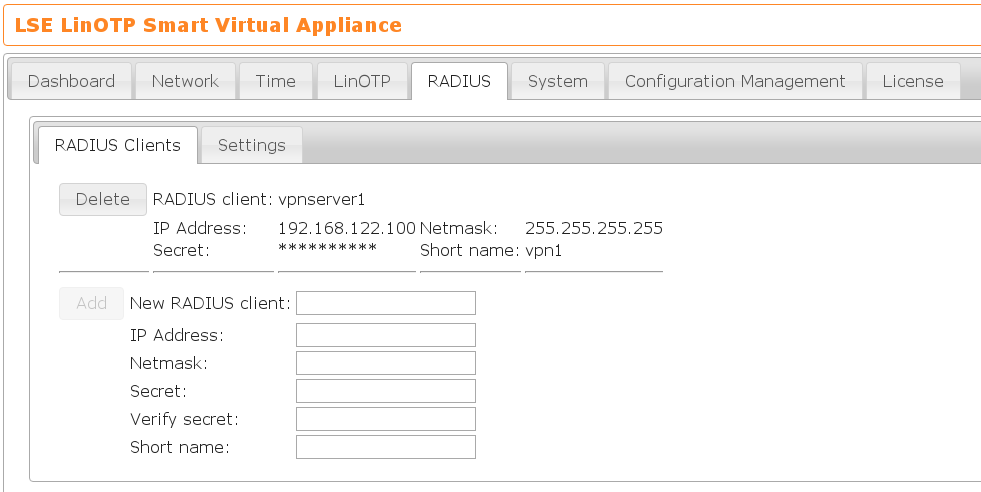
on the tab RADIUS → Clients. The client definition can contain a complete
subnet. E.g. you can configure that the whole subnet 192.168.122.0/24 may access
the LinOTP RADIUS server using a common secret. This secret must be included in
the configuration of the RADIUS client(s). You can define many different RADIUS
clients, but each should have a unique identifying name.
E.g. if you want to have only one client access the LinOTP RADIUS server, you could specify 192.168.122.100/32, so that only the host 192.168.122.100 may access the RADIUS server.
Each RADIUS client definition may be given an optional short name. This is
an identifier you can use to refer to in the detailed RADIUS definitions.
4.7.1. Detailed settings#
Detailed RADIUS settings can be defined on the tab RADIUS → Settings.
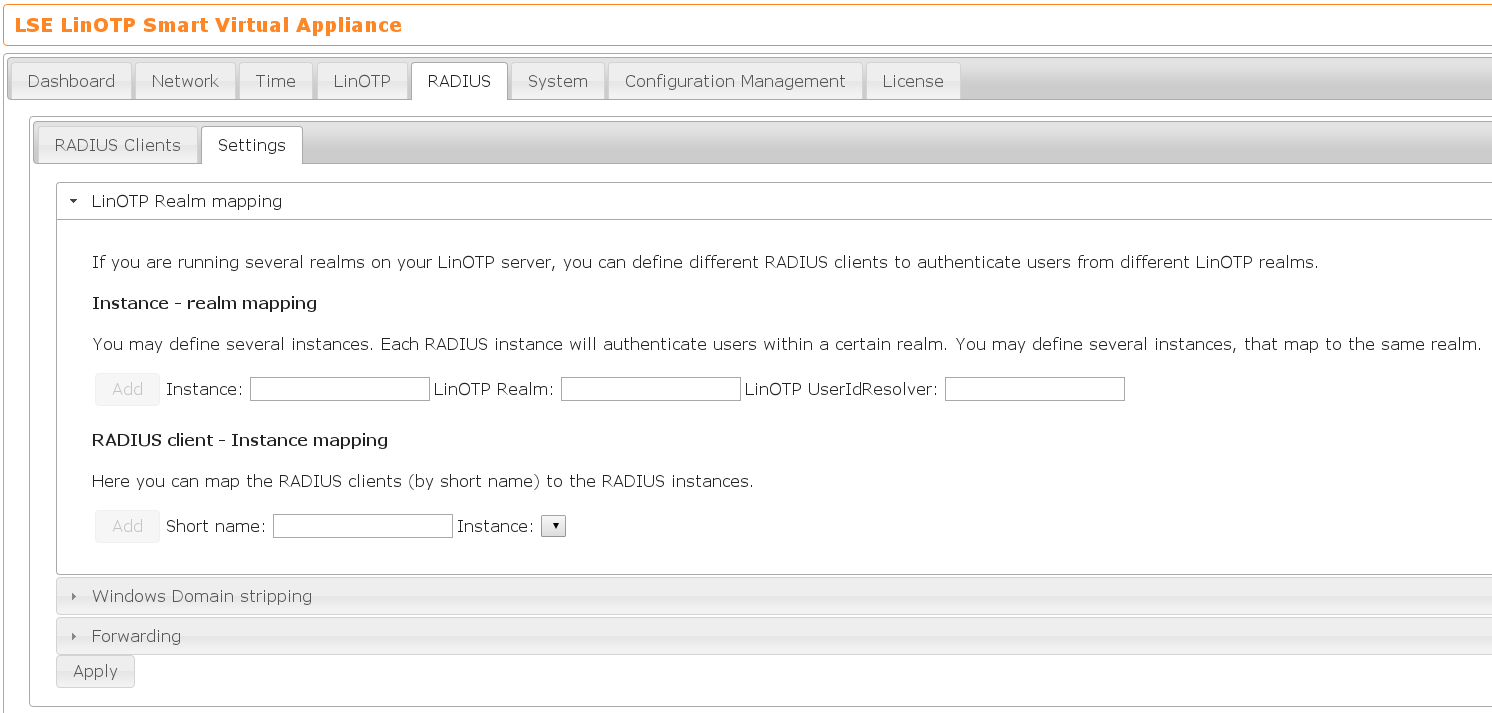
Realm mapping#
Using the Realm mapping you can map a realm to RADIUS clients, i.e. you can define, that only a specified realm should be allowed to login to certain RADIUS clients.
This is a two-step process.
You need to map a realm to a RADIUS LinOTP instance. This will define a RADIUS internal instance, that can be used for further RADIUS policies.
In the second step you need to map the RADIUS client as defined by the short name to this internal RADIUS instance.
Windows domain stripping#
Some RADIUS clients will send the Windows domain with the RADIUS username. LinOTP usually only handles the username without FQDN. Some RADIUS clients may send
NT-DOMAINusername
NT-DOMAIN/username
Note
By default LinOTP interprets the @-sign as a delimiter between username and LinOTP realm name. So if your Windows domain matches your LinOTP realm names, this can be an intended behavior.
